The total cyber security market is valued at USD 136 billion as on 2017 and is likely to reach USD 262 billion by the end of 2023, growing at a CAGR of 11.5%. The increasing frequency of cyber-crimes along with mandates to regulatory compliances, and development of new applications such as internet of things (IOT), cloud, mobility, Machine-to-Machine (M2M) are some of the major factors contributing towards the growth of cyber security market. There are companies investing heavily on digital transformation and in this process they have to prevent e-commerce fraud which involves complex threat detection system. In the current scenario, there is huge potential in the cyber security market because, the ransomware attacks have doubled the frequency from 13% to 26% and the losses due to these attacks is estimated more than 5 billion USD.
The cyber security market is dominated by North American market which approximately accounted for half of the global market. North American region will experience high growth as the government allocates the budget for security of critical infrastructure & sensitive data. The US government has spent around $ 14 billion on cyber security in 2016 and is planning to spend around US $ 19 billion in 2017.
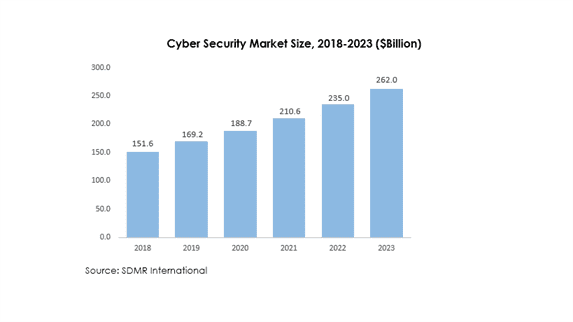
The application security is anticipated to be the fastest-growing segment with a CAGR of around 19% from 2017 to 2023. The losses due to data breach per incident has increased upto $4 million per incident. Moreover, the IT spending for application security is less than 5%, which provides huge potential for the growth of the cyber security market.
The various end-user industries of cyber security market are healthcare, government, financial services, telecommunications, transportation, retail, manufacturing, aerospace and others. Banking and Financial services will experience the highest CAGR from 2018-2023 mainly due to shifting of banks towards digital channels such as online banking and mobile transactions.
The companies are strengthening their market presence by acquiring service providers and widen their product portfolio. In June 2017, Microsoft announced the acquisition of U.S. based company Hexadite which will assist them in commercial customers detect responses in Windows 10 - specifically along with the addition of Hexadite's end-point security automated remediation. The major players in this market are Booz Allen Hamilton, Hewlett Packard Enterprise, IBM International, Verizon Communications, Mcafee LLC, Trend Micro, Inc., Symantec Corporation, Lockheed Martin, Cisco Systems, Inc., Fortinet, Inc., Check Point Software Technologies, Palo Alto Networks, Inc., Juniper Networks, Inc., Northrop Grumman, Sophos Ltd., Optiv, Fireeye, Inc. and others.
1 Introduction
1.1 Goal & Objective
1.2 Report Coverage
1.3 Supply Side Data Modelling & Methodology
1.4 Demand Side Data Modelling & Methodology
2 Executive Summary
3 Market Outlook
3.1 Introduction
3.2 Current & Future Outlook
3.3 DROC
3.3.1 Drivers
3.3.1.1 Demand Drivers
3.3.1.2 Supply Drivers
3.3.2 Restraints
3.3.3 Opportunities
3.3.4 Challenges
3.4 Market Entry Matrix
3.5 Market Opportunity Analysis
3.6 Market Regulations
3.7 Pricing Mix
3.8 Key Customers
3.9 Value Chain & Ecosystem
4 Market Demand Analysis
4.1 CyberSecurity Market, By Solutions/Product
4.1.1 Identity Authentication Access Management (IAAM)
4.1.1.1 Identity Access Management (IAM)
4.1.1.2 Web Access Management
4.1.2 Infrastructure Protection
4.1.2.1 Security and Vulnerability Management
4.1.2.2 Data Loss prevention
4.1.3 Network Security Protection
4.1.3.1 Encryption
4.1.3.2 Antivirus/Anti-Malware
4.1.3.3 Firewall
4.1.3.4 Unified Threat Management
4.1.4 Security Services
4.1.4.1 Security Information and Event Management/Managed Security Services
4.1.4.2 Risk and Compliance Management/Enterprise Risk and Compliance
4.1.4.3 Disaster Recovery
4.1.5 Others
5 Cybersecurity Market Analysis, By End-User
5.1 Introduction
5.2 Healthcare Sector
5.3 Government
5.4 Financial Services
5.5 Telecommunications
5.6 Transportation
5.7 Retail
5.8 Manufacturing
5.9 Aersopace
5.1 Others
5.1.1 Professional Services
5.1.2 Managed Services
6 Cybersecurity Market Analysis, By Organization Size
6.1 Small and Medium Enterprises
6.2 Large Enterprises
7 Cybersecurity Market Analysis, By Deployment
7.1 Cloud
7.2 On-Premises
8 Cybersecurity Market Analysis, By Security
8.1 Application Security
8.2 Data and Information Security
8.3 Endpoint Security
8.4 Cloud Security
8.5 Others
9 Cybersecurity Market Analysis, By Region
9.1 North America
9.1.1 US
9.1.2 Canada
9.1.3 Mexico
9.2 Europe
9.2.1 Germany
9.2.2 Italy
9.2.3 France
9.2.4 UK
9.2.5 Rest of Europe
9.3 Asia Pacific
9.3.1 China
9.3.2 Japan
9.3.3 India
9.3.4 Australia
9.3.5 Singapore
9.3.6 Rest of APAC
9.4 Middle East & Africa
9.4.1 Saudi Arabia
9.4.2 UAE
9.4.3 Rest Of MEA
9.5 South America
9.5.1 Brazil
9.5.2 Argentina
9.5.3 Rest of South America
10 Supply Market Analysis (Industry Player Analysis)
10.1 Strategic Benchmarking
10.2 Market Share Analysis
10.3 Key Players
10.3.1 Booz Allen Hamilton
10.3.2 Hewlett Packard Enterprise
10.3.3 IBM International
10.3.4 Verizon Communications
10.3.5 Mcafee LLC
10.3.6 Trend Micro, Inc.
10.3.7 Symantec Corporation
10.3.8 Lockheed Martin
10.3.9 Cisco Systems, Inc.
10.3.10 Fortinet, Inc.
10.3.11 Check Point Software Technologies
10.3.12 Palo Alto Networks, Inc.
10.3.13 Juniper Networks, Inc.
10.3.14 Northrop Grumman
10.3.15 Sophos Ltd.
10.3.16 Optiv
10.3.17 Fireeye, Inc.
10.3.18 Other Players
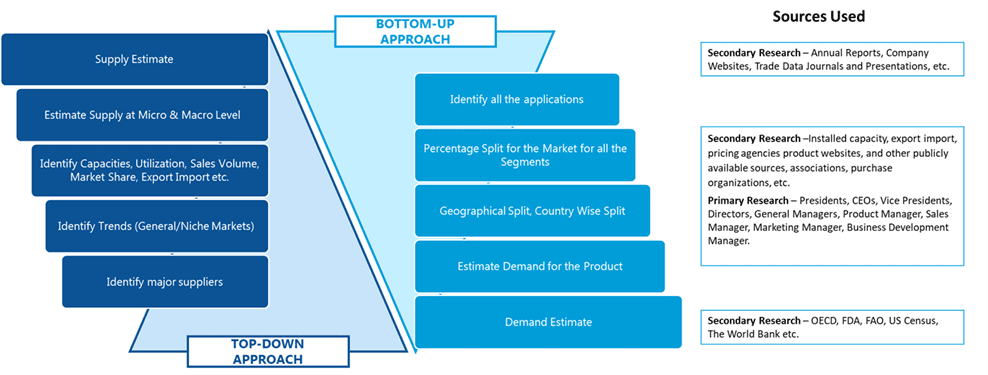
SDMR employs a three way data triangulation approach to arrive at market estimates. We use primary research, secondary research and data triangulation by top down and bottom up approach
Secondary Research:
Our research methodology involves in-depth desk research using various secondary sources. Data is gathered from association/government publications/databases, company websites, press releases, annual reports/presentations/sec filings, technical papers, journals, research papers, magazines, conferences, tradeshows, and blogs.
Key Data Points through secondary research-
Macro-economic data points
Import Export data
Identification of major market trends across various applications
Primary understanding of the industry for both the regions
Competitors analysis for the production capacities, key production sites, competitive landscape
Key customers
Production Capacity
Pricing Scenario
Cost Margin Analysis
Key Data Points through primary research-
Major factors driving the market and its end application markets
Comparative analysis and customer analysis
Regional presence
Collaborations or tie-ups
Annual Production, and sales
Profit Margins
Average Selling Price
Data Triangulation:
Data triangulation is done using top down and bottom approaches. However, to develop accurate market sizing estimations, both the methodologies are used to accurately arrive at the market size. Insert Image


